“I’ve been hacked!” I thought with a panic, closing yet another window. No matter what page I tried to open, no matter how reputable, I ended up in the spam and click-bait universe. My browser was possessed.
Your flash player is out of date! Update now!!!
You won’t believe this neat trick…
I panicked. I couldn’t use my laptop and I worried that the infection would spread. Nothing like this had ever happened to me before.
“What’s going on? Did I get infected with some virus?
yours truly, panicking
Is my whole home network compromised?
Where is this coming from?”
I ran antivirus and antimalware scans. I tightened up my router security. I set up OpenDNS to enforce web filtering. And of course, I turned off and on again. None of those methods helped. Something else was going on.
Calmer head is a smarter head
Once the initial panic wore off, I looked at my problem with a clearer head. It appeared that not being able to get to the pages I wanted to on the first click was the only unhealthy symptom my laptop was experiencing. I tried something which probably should have been my first step. I used a different browser.
I used Firefox instead of Chrome and it worked! I was able to navigates all websites as normal. That reassured me that the problem was limited only to using Chrome browser. I was getting closer to the solution.
What’s wrong with Chrome?
I had been using Chrome for many years and never had issues like this, so I tried to think back to what might have changed recently. Then, I remembered that few days before, I installed some new Chrome extensions. I use several extensions for different needs, like a pop-up blocker, which saves me many a headache from the ad overload, or Grammarly, which saves me from embarrassing spelling typos. Most recently, I had added two more: TTSReader and iReader. Could it have been one of them?
TTSReader is a text to speech app. I had used their site ttsreader.com for a long time with no issues, so I doubted that their Chrome extension was causing unwanted behavior.
I was new to the iReader extension but loved it already. It worked beautifully. It stripped down sites to the bare content, removing all ads and images leaving only easy to read, pleasantly formatted text.
Could something so nice be so bad?
Chrome extensions are small programs serving the role of tools for your browser. Just like apps on a phone, they can be free or paid. They can block pop-ups, check your spelling, manage your passwords or change the look of the sites you visit to your liking. In essence, they are convenience tools.
There was only one way to find out. I navigated to my Chrome extensions and removed iReader.
Result: blissful quiet. I was finally able to browse the web without being redirected to malicious sites. The crises was over.
Problem behind the scenes
Most Chrome extensions are very useful and beneficial but among them hide those developed with malicious intent. In the case of this story, a bad extension hijacked user’s browser redirecting all web traffic. Instead of ending up on familiar websites, user found herself on unwanted pages. Judging from the type of content on those redirected sites, I suspect that there were several motivations behind this activity:
- Redirecting to click-bait sites (“10 sure ways to loose weight,” “You won’t believe what happened next”). These sites generate revenue from ads placed on their pages. The more users go on their site, the more pages they open, the more ad revenue they’ll earn.
- Redirecting to a site prompting the user to download something (“Your Java is outdated,” “You’re computer is infected! Click here to run antivirus scan”). These sites aim to have the user download a malicious program. This program could be a virus, spyware or more adware.
Malicious browser extensions are not the only method of browser hijacking and Chrome is not the only web browser that suffers from this problem. If you’re experiencing similar issues, you end up on sites you didn’t mean to go to or you think your search results are modified, I suggest below nice write-up by Bleeping Computer with tips on removing different types of browser redirects. Good luck.
How to Remove a Web Browser Redirect Virus
The cycle of madness
It has now been nearly a year since that incident. When it originally happened, I immediately reported the malicious behavior of the iReader extension to Chrome Web Store hoping that they would take action and remove it from available extensions so no one else would fall for that trap.
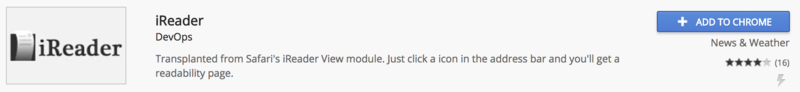
Following up on it now, in July 2018, I see the same extension is still listed.
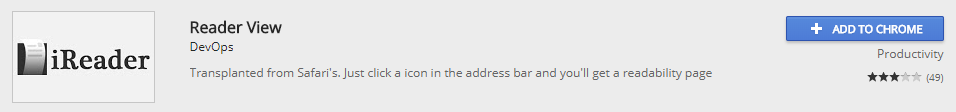
Notice that the description slightly changed and they also renamed it to Reader View. It’s possible that they removed the original extension I reported to Google but promptly replaced it with a copy. Just look at the reviews people have left for it. It’s still malicious! It modifies Google search so you would see links to their ads instead of actual Google search results.
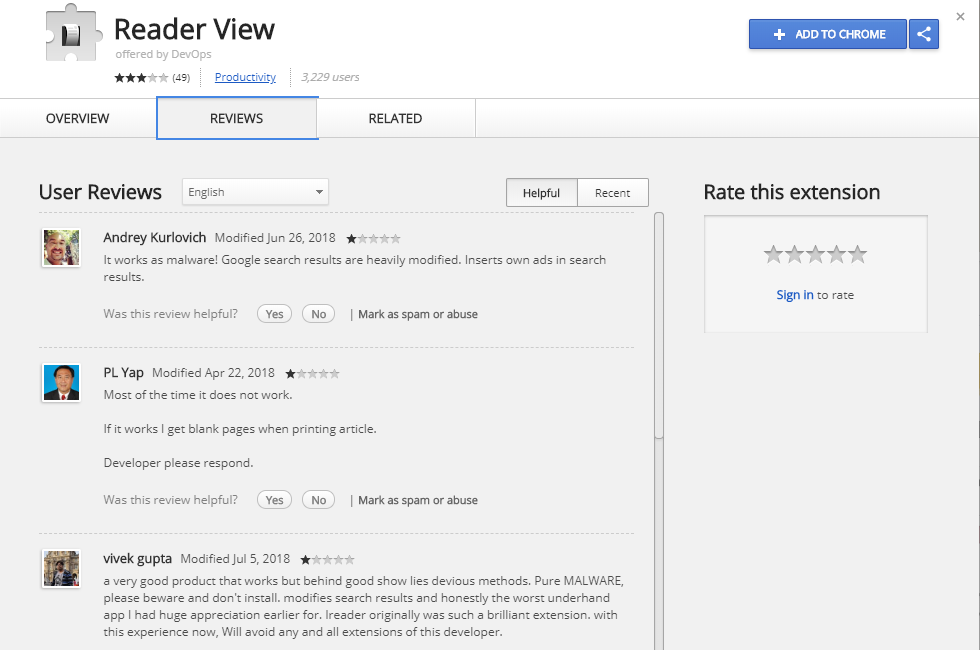
This isn’t the only bad extension
Malicious apps seem to have become a new business model to some. Just imagine if this developer placed several of those malware extensions on the Chrome Web Store, each doing a different function to capture as many users as possible. If even only some of those users click on few of their links, developer gets ad revenue. Multiply that by all of the malicious activities they do and you might end up with a sizable passive income. The only work they have to do is to recycle the same extension under a new name every few months to start fresh user reviews. And the cycle begins anew.
Here’s what else this developer has on the Chrome Web Store:
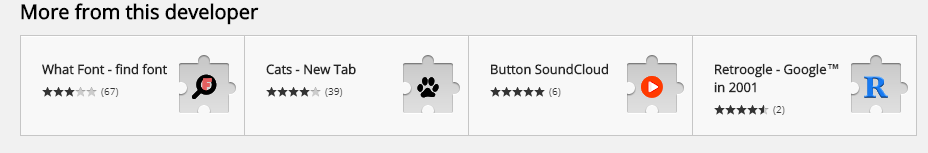
Looking at the descriptions of each of these extensions, they seem to be similar to Reader View but with even more open approach. For example, “Retroogle – Google in 2001” claims to give you the old look of Google and “Cats – New Tab” gives you a search box and a cat gif. Although user reviews don’t reflect that yet, I’m guessing that the search box in both will lead you to modified search results. It is in fact the same ad injection method as the iReader hiding under a different disguise.
The other two apps have reviews saying that they don’t work well at all which prompts me to believe that they do something even more suspicious. Maybe they act as spyware collecting user data to sell off to data collection companies? I can only speculate.
Unfortunately, it seems that malicious apps are the only apps this developer has put on the Web Store. Further proof is the link to their privacy policy. It was obviously copied from a template, complete with: “If you have any questions about this Privacy Policy, please contact us at this emai@gmail.com.” I wish that Google made it possible to report developers like this one, not just individual extensions, so all extensions they offered could be flagged for removal.
A widespread problem
Stories of extensions gone rogue are becoming more and more common. In this article, for example, Bleeping Computer editors expose a story of a company who buys popular (good) extensions and adds ad injection to them (“Particle” Chrome Extension Sold to New Dev Who Immediately Turns It Into Adware). The worst part of this method is that users that had been successfully using the good extension before it was bought will have a hard time investigating the cause of the unwanted behavior. They would not suspect a tool they’ve used for years.
On a similar note, in this Reddit interview, I am one of the developers of a popular Chrome extension and we’ve been approached by malware companies that have tried to buy us. AMA!, a developer of a popular extension, Honey, explains behind the scenes offers developers get to sell out their extension and user data.
Everybody loses in the end
Gemusan, Developer of Honey
On the one hand, I am very disappointed with Google’s standards for what is an acceptable browser extension. On the other hand, there will be negative consequences if Google takes drastic measures to control this chaos. As Honey developer points out, “This is incredibly dangerous for the extension ecosystem in general. This kind of activity will force the platforms (Chrome store and Mozilla store) to be more and more restrictive, in turn taking away browser extension’s ability to do anything meaningful. Everybody loses [in] the end.”
While Honey promises that they will never sell out, many other developers might make the “easy cash” choice and accept a buyout (like this one) or agree to add malicious code to their extension for a monthly fee.
We shouldn’t be [called] awesome because we refuse to be shady.
Gemusan, developer of Honey, responding to a user praising them for their ethics
That should be expected.
Is this the binary future we are heading into? Either Malware infested Chrome Web Store or extensions that are secure but so limited in functionality that there’s no point in installing them?
What does Google have to say about this?
I’m glad to find out that Google has been leading the efforts of discovering malware in extensions for several years. using machine learning to detect malicious behavior and investigate distribution methods. Per their 2015 publication, Trends and Lessons from Three Years Fighting Malicious Extensions, malicious extensions they discovered and removed comprised 10% of all available in the Web Store at the time. However, this effort is never ending. As browsers implement new security measures, the extensions are developed with more sophisticated methods to overcome them.
Protect yourself from malicious extensions
In this endless cat and mouse game, there’s an important lesson to the user. Maybe we don’t ask ourselves often enough “Do I really need this?”
We mustn’t become insensitive to the technologies we use. We are constantly bombarded with the requirement to accept terms and conditions. Your only option seems to be that you can’t use the technology you need and have privacy at the same time. However, we shouldn’t give up. No matter how many data breaches have happened, how much of our personal information is out there available for purchase without our explicit consent, we still have a say in our future actions. We need to be vigilant and question what permissions a browser extension or a phone app requests. If it doesn’t make sense, like a calculator tool requiring your contact list, we shouldn’t accept them.
So, as a healthy browser exercise, I suggest we all take a look at our extensions today. Type in chrome://extensions/ in your address bar and click on Details link by each one. Check what Permissions it requests. If it seems off or if you don’t even use that extension, click Remove. It’s never too late for spring cleaning. Your browser will thank you.